Recently, Cloudflare has made several adjustments to its bot protection systems. One of Turnstile’s key strengths was that once it determined the browser was trustworthy based on its fingerprint, it would automatically check the “Verify you are human” box. Unfortunately, that’s no longer the case. Even when using your regular phone or PC to visit a site protected by Cloudflare Turnstile (e.g., indeed.com), after a few seconds of loading (during which you see the message “Verifying”), the checkbox is no longer clicked automatically. Now, Cloudflare requires you to click the checkbox manually, likely to analyze your mouse movements and further assess whether you’re a bot or a human.
A few months ago, Cloudflare frequently toggled this feature on and off, but it now seems permanent. We ran several internal tests to audit our fingerprint masking technology and encountered the issue of needing to click the checkbox programmatically. However, this is no easy task, as Cloudflare continues to make it harder to automate this step with Playwright.
The checkbox lives in a cross-domain, sandboxed iframe. Turnstile renders its widget inside an <iframe> whose src is served from Cloudflare’s domains. By default, you can’t just do page.click("input[type=checkbox]") on the parent page - you first have to locate the iframe, obtain its Frame object, and then issue clicks inside it. On top of that, the checkbox itself is buried under one or more Shadow Roots inside that iframe. Cloudflare wraps its markup in a locked Shadow DOM to encapsulate styles and behavior, meaning you can’t traverse it with ordinary DOM queries. Many folks simply never see the iframe or can’t attach to it, so their selectors never match.
You’ll often find blog posts advising you to locate the Turnstile iframe by its source or access its shadow root. While that might work today, Cloudflare could rename the custom element or add another shadow boundary tomorrow, breaking your “magic” selector instantly.
Solution
My long-term solution for clicking the Cloudflare Turnstile checkbox is to use image recognition (OpenCV) to find its coordinates and click it. Below, I’ll demonstrate how.
Please note that to ensure the code works, you need to integrate Playwright with Kameleo so that Cloudflare does not detect you’re using an automated browser based on its fingerprint.
Locate the Cloudflare Turnstile Checkbox
An example project is available in our GitHub repository, which includes images of the Cloudflare Turnstile widget (both light and dark mode). Once your Playwright script visits a site protected by Turnstile, you pass a screenshot to OpenCV, which locates the entire Turnstile frame using these images. OpenCV can then find the checkbox within that frame.
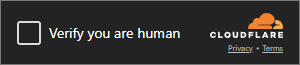
Because the checkbox itself isn’t unique enough to be located in a full-page screenshot, we first locate the Turnstile frame and then locate the checkbox inside it.

const fullScreenshotBuffer = await page.screenshot({ fullPage: true });
const { x: clickX, y: clickY } = await locateClickPosition(fullScreenshotBuffer);Click the Cloudflare Turnstile Checkbox
Now that we have the X and Y coordinates of the checkbox, we can click it from Playwright:
await page.mouse.move(clickX, clickY, { steps: 10 });
await page.mouse.click(clickX, clickY);When I wrote this article, this method was working reliably. However, for a long-term solution, consider using Ghost-cursor to make the click appear more human-like. The GitHub example uses GhostCursor:
cursor = await createCursor(page);
await cursor.actions.move({ x: clickX, y: clickY });
await page.waitForTimeout(300);
await cursor.actions.click();Humanize your automated browser
To ensure Cloudflare doesn’t detect your automated browser, using Playwright alone is insufficient. The solution above only works if you enable stealth mode. Otherwise, even if you manage to click the checkbox, the captcha will reload.
The simplest way is to use Kameleo’s anti-detect browser. Our custom-built browsers (Chroma and Junglefox) prevent automation detection in Playwright, Puppeteer, and Selenium. They mask your browser fingerprint by loading fresh, real fingerprints, helping you stay undetected.
Code example
The full project is available on GitHub.
The linked video also shows that this method does not work with regular Playwright.
To ensure that OpenCV can be installed on your PC you need to make sure, that CMake and Visual Studio’s “Desktop development with C++” is installed as well.
Install CMake with the following command:
choco install cmake--installargs 'ADD_CMAKE_TO_PATH=System'Install Visual Studio Tools from Microsoft’s website. During installation make sure you select “Desktop development with C++”
See the Setup & Run section in our GitHub repository for details.